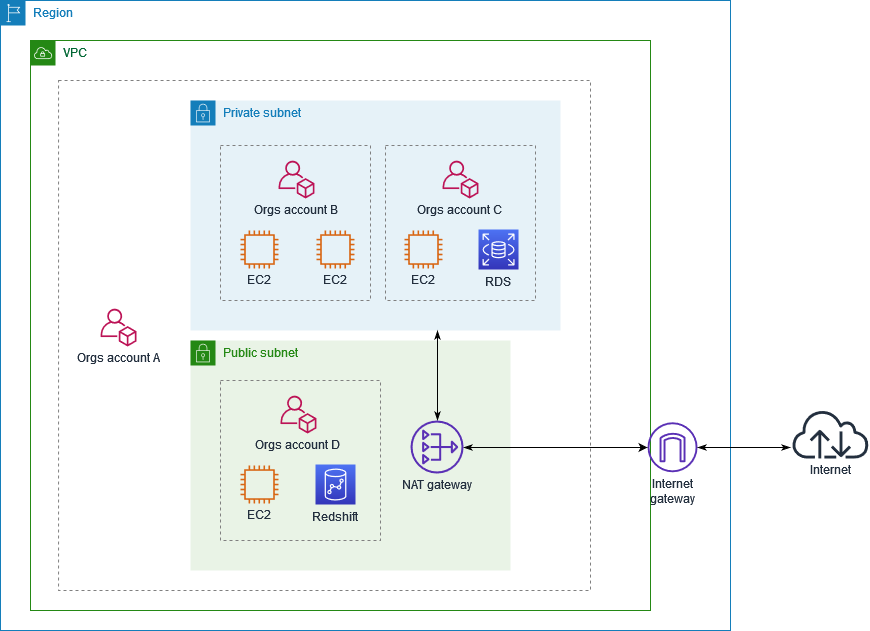
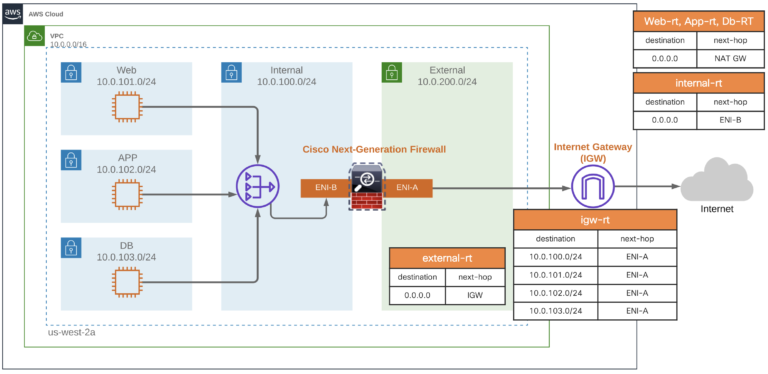
Running queries securely from the same VPC where an Amazon Redshift cluster is running | AWS Big Data Blog

Screening Eagle: Optimize CI/CD and end user experience in Amazon AppStream 2.0 | Desktop and Application Streaming

Configuring low latency connectivity between AWS Outposts rack and on-premises data using CoIP | AWS Compute Blog

How to Monitor Host-Based Intrusion Detection System Alerts on Amazon EC2 Instances | AWS Security Blog

Access web interfaces securely on Amazon EMR launched in a private subnet using an Application Load Balancer | AWS Big Data Blog

How Munich Re Automation Solutions Ltd built a digital insurance platform on AWS | AWS Architecture Blog

Disaster recovery considerations with Amazon EMR on Amazon EC2 for Spark workloads | AWS Big Data Blog